In vulnerability scanners or penetration testing reports, you might come across statements like “Service version x.y.z is vulnerable to CVE-YYYY-ABCD." However, it’s essential to delve deeper to confirm the actual vulnerability.
Let’s consider a real example:
We received a vulnerability report indicating a vulnerability ( CVE-2023-23916 ) in curl v7.74.0 within the Debian 11 environment.
The CVE documentation mentions:
Affected versions: curl 7.57.0 to and including 7.87.0
At first glance, it appears that v7.74.0 is indeed vulnerable. But is that really the case?
It’s important to understand that in Long-Term Support (LTS) releases, the updates are limited to specific versions, and you might not always have the latest version of a package.
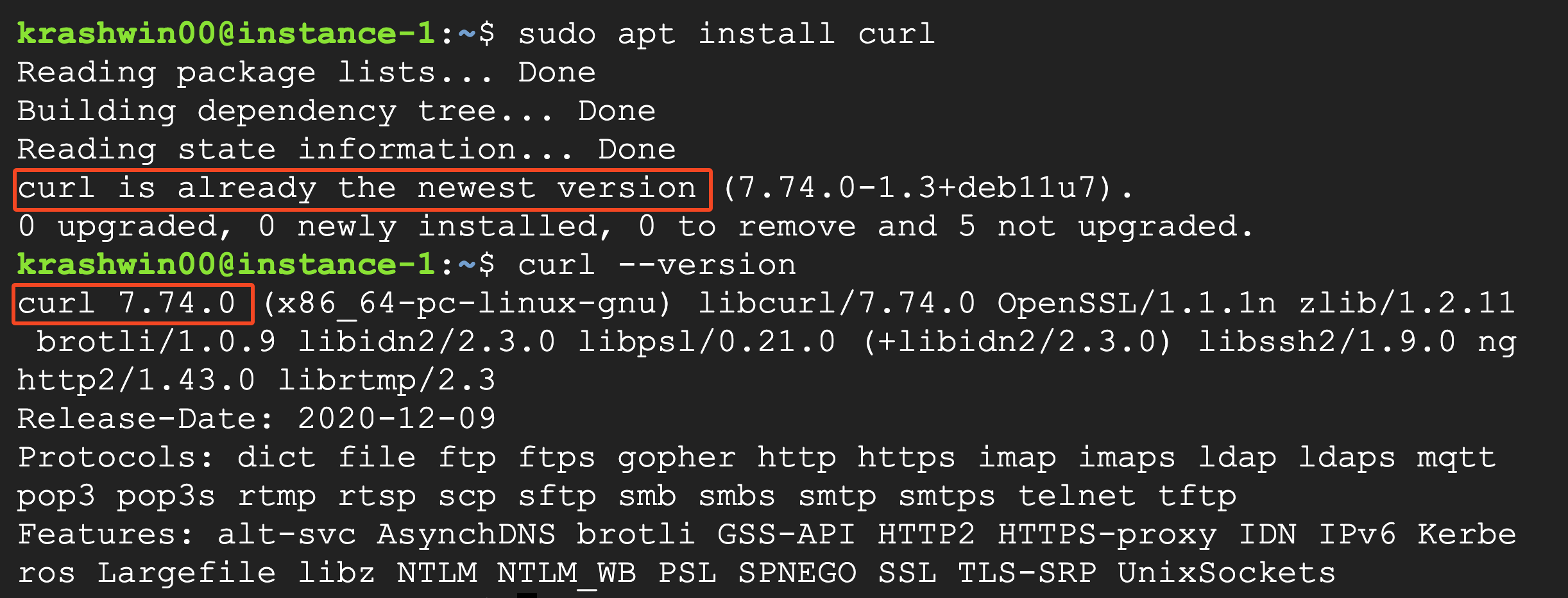
In the above image, you can see that it says “curl is already the newest version.” However, the actual latest version of curl is 8.2.1 , indicating that the maximum version available for Debian 11 is curl 7.74.0.
Now, how do we determine if the curl version in Debian 11 is vulnerable?
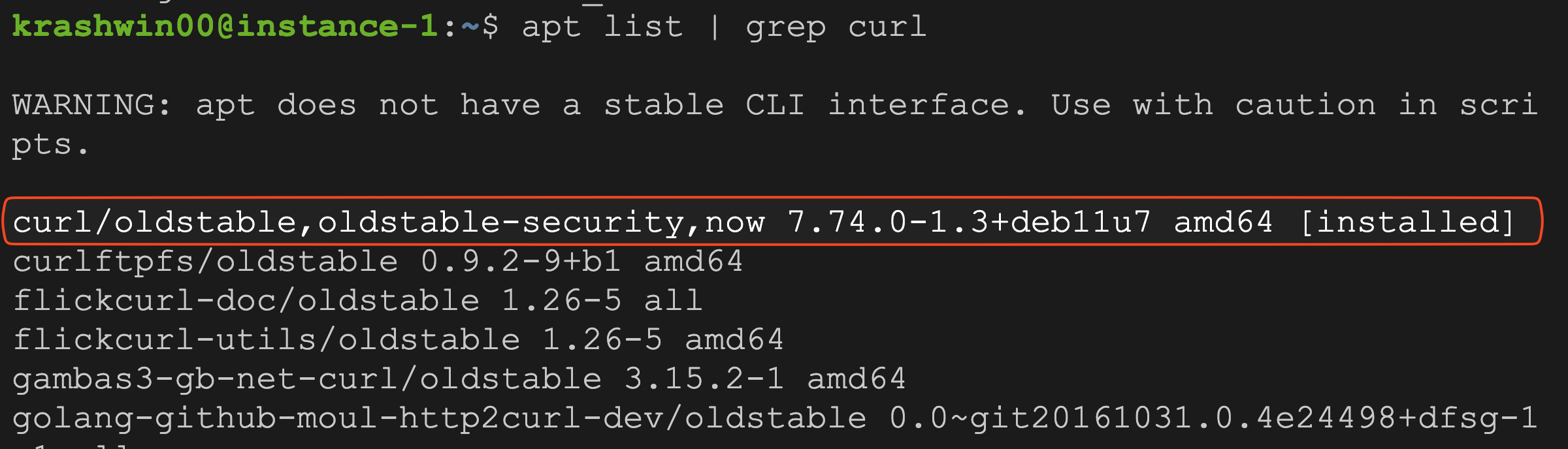
The installed curl version is 7.74.0-1.3+deb11u7. To check if this version is secure/vulnerable, we need to review its changelog.
How to see the changelog?
- Navigate to https://www.debian.org/distrib/packages .
- Use the
Search Packages Directory
to find the package for your OS version.
- Select the appropriate OS version from the “Limit to suite” section at the top of the page.
- Find the curl package and view its changelog.
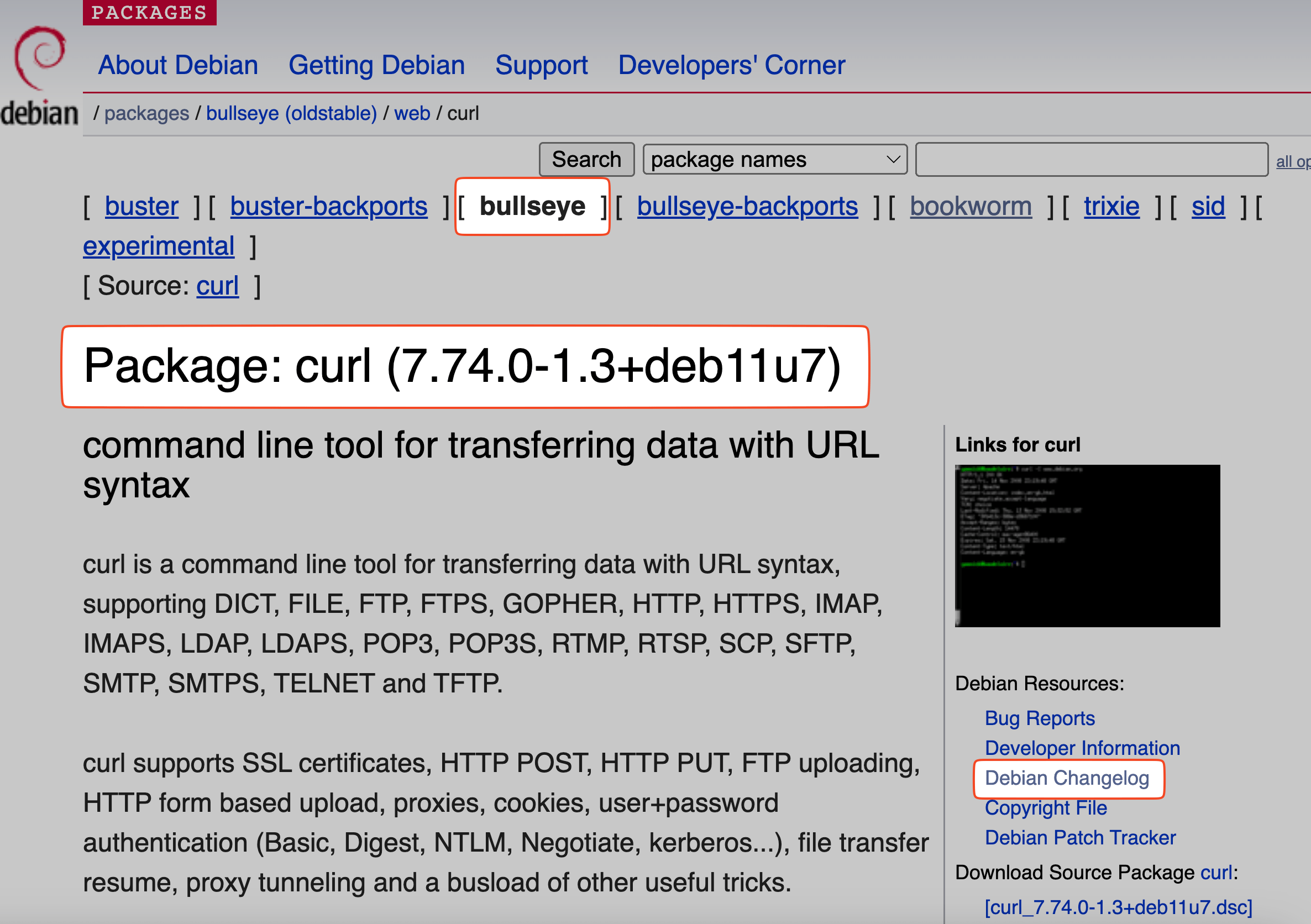
- Search for the CVE to see if it has been fixed in any updates.
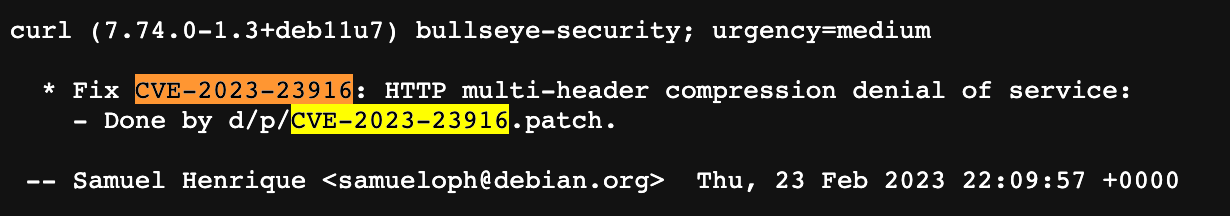
From the changelog, we can observe that the installed curl version, 7.74.0-1.3+deb11u7, has been patched with the necessary security fixes, rendering the vulnerability invalid for this version.
Therefore, it is crucial to validate reported vulnerabilities for specific software versions by verifying the presence of security patches in the changelog before taking any action based solely on the initial report.
Hope this will help in triaging vulnerabilities reported by scanners and penetration testing reports, enabling you to handle security issues with greater ease and confidence.
Until next time!
